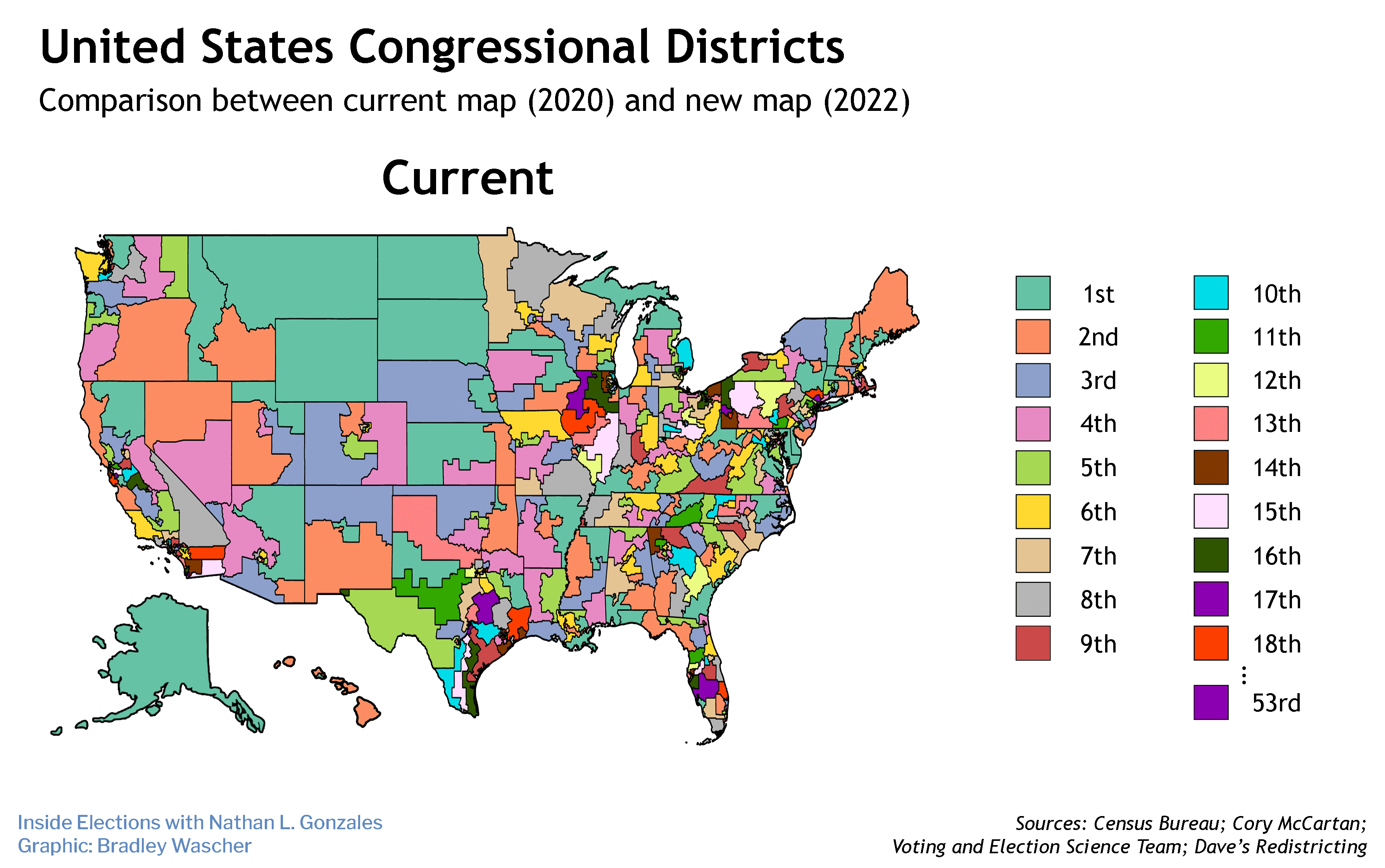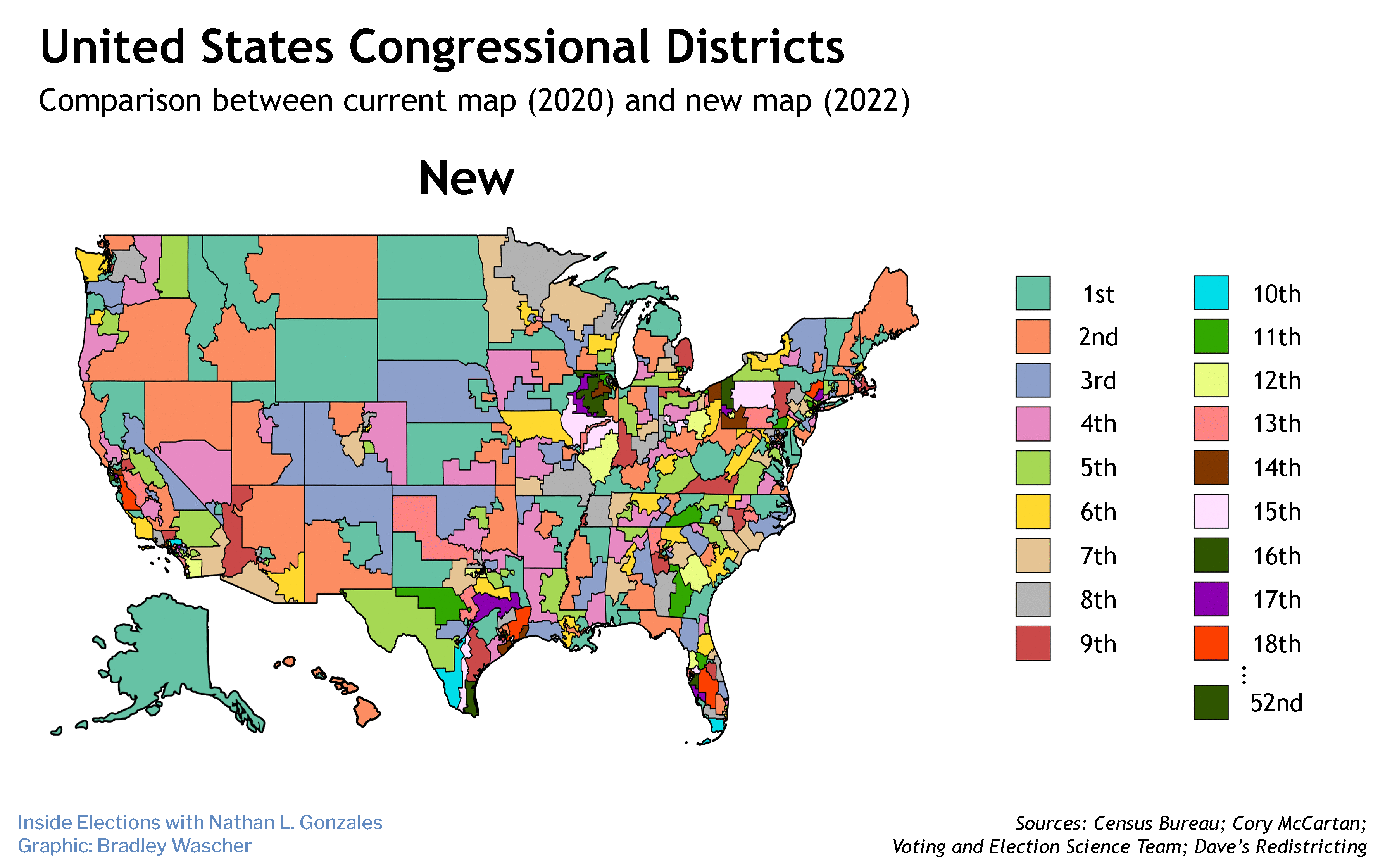
The first votes of the presidential election will be tabulated after the Iowa caucuses next month using the sort of internet-connected system that worries election security experts. They say preventing the sort of interference that sullied the 2016 election should be more of a priority than speed in compiling the returns.
But the Iowa Democratic Party plans to deploy a smartphone app to officials running the caucuses across the state for use in calculating and transmitting the results the night of Feb. 3. Putting such vote totals into cyberspace makes them readily vulnerable to nefarious hacking.
Party leaders say they are aware of the potential problems but believe their system will repel them. If that doesn't happen, the opening round of the intense contest for the Democratic nomination will be condemned to global ridicule.
The aim of the new app is to get the caucus results to the public quicker, Troy Price, the chairman of the state party, told Iowa Public Radio. He declined to detail how the app was designed, or by who, or what has been done to guarantee security.
He said the state party worked with the national party's cybersecurity team, and with Harvard University's Defending Digital Democracy project. But Price declined to say whether any third party has investigated the app for vulnerabilities, as many cybersecurity experts recommend.
Unlike many states in which local and state officials oversee presidential primaries, in Iowa the responsibility for administering, staffing and funding the caucuses rests with the state party, which in turn relies mainly on unpaid volunteers.
The Iowa Democrats' plan is for caucus leaders to compile the results from the in-person gatherings and send them to party headquarters in Des Moines using their smartphone apps — assuming the software works and the network does not become overwhelmed or compromised. In the past, making a telephone call was the default method, and phones will still be used as a backup this time.
Because caucusing and the climactic vote counting in hundreds of locations are open to the public, it's highly unlikely a hack to alter the results would go unnoticed. But the damage to the public confidence in the 2020 elections would likely be catastrophic.