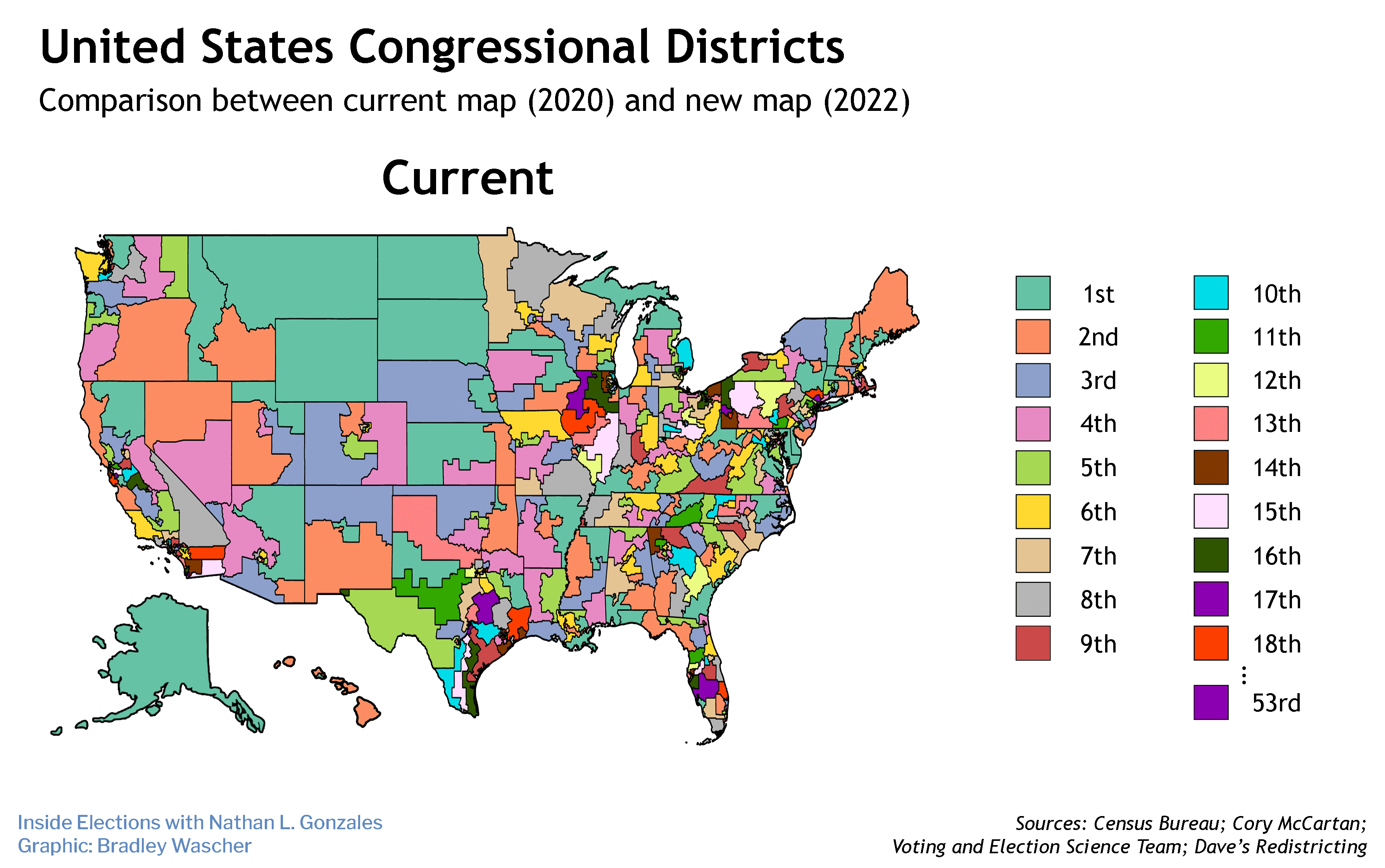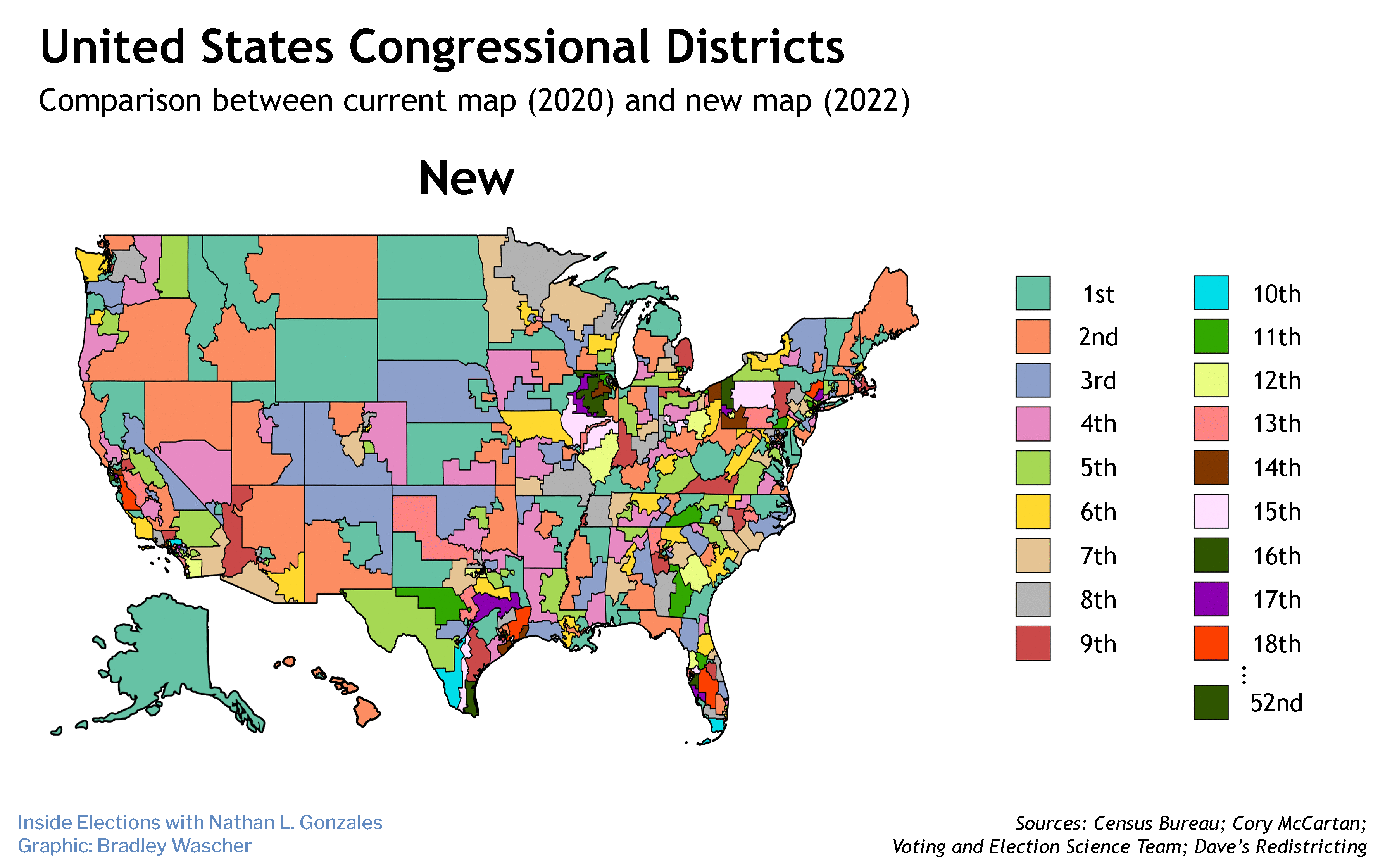
Along with the candidates and the issues, the 2020 presidential election is also going to be about the voting process itself.
Russian efforts to hack into the voting systems of 2016 have boosted election security to a critical concern this time, prompting states to spend tens of millions buying new equipment, hiring cybersecurity wizards and installing software that warns of intrusions — among numerous other steps. More purchases of hardware, software and expertise are coming in the months ahead.
Whether enough money gets spent, and wisely, won't be known for sure until Nov. 3, 2020 — when the system will be subject to the one test that really matters. And whether the country decides the presidential election result is trustworthy will likely come down to how reliably things work in the relatively small number of states both nominees are contesting.
[ Swing states build 2020 hacking protections: Will they hold?]
With 11 months to go, The Fulcrum reviewed information from state elections officials, the National Conference of State Legislatures, the Election Assistance Commission and news reports to get a sense of the election security landscape. Here's the state of play in the 13 states likeliest to be presidential battlegrounds.
Test your election security knowledge with our quiz.
Arizona

Hacking in 2016: Attempted but not successful. Cybercriminals stole login credentials to Arizona's voter registration database in 2016 but could not break into the database itself. Russian intelligence officers also used a computer located in Arizona to help transfer information stolen from hacked national Democratic Party computers.
Security enhancements since: The state created a multifactor login system to safeguard voter registration records and is building a new voter registration database.
Voting paper trail: Balloting equipment must generate a voter-verifiable paper record.
Spending federal grants: To create the new voter registration database.
Quote: "We got lucky," Michele Reagan, Arizona's GOP secretary of state in 2016, said of the failed hacking attempts. "We had a real wake-up call with that."
Colorado
Hacking in 2016: None identified, but the Homeland Security Department says Colorado was one of 21 states probed for vulnerabilities by the Russians.
Security enhancements since: The state is considered a model and was tackling election vulnerabilities before Russia's attempts. It was the first state to conduct rigorous post-election audits. Election officials take part in security training.
Voting paper trail: State-of the-art election machines have recently been deployed statewide. All use paper ballots or generate a voter-verifiable paper record.
Spending federal grants: To enhance technology and security in election systems, including improving risk-limiting audits and hiring IT officials.
Quote: "This was a scan," the GOP secretary of state in 2016, Wayne Williams, says in downplaying the Russian visits to state election sites. "It happens hundreds, if not thousands of times per day."
Florida
Hacking in 2016: Yes, and it was not disclosed until special counsel Robert Mueller's report in April. In a follow-up meeting, FBI and Homeland Security officials told GOP Gov. Ron DeSantis that voter registration systems were breached in two counties, but he wasn't told which ones. This summer the Senate Intelligence Committee raised the number of counties to four, but their identities remains officially undisclosed. No votes were affected by the hacking, authorities said.
Security enhancements since: All 67 counties are now equipped with an intrusion detection system. The state was one of the first to have all its counties signed up for an alert and information sharing system. In his budget proposed last month for the year beginning next July, DeSantis is asking for $6.6 million for election security including the hiring of 10 cybersecurity experts.
Voting paper trail: Paper ballots are required and in use statewide.
Spending federal grants: To modernize voting systems and upgrade the security of the state's voter registration system.
Quote: "When it comes to meddling in elections, we expect Vladimir Putin to keep secrets from the American public. We don't expect the U.S. government to behave like the Kremlin," the Orlando Sentinel wrote in an editorial complaining about federal officials refusing to identify the hacked counties.
Georgia
Hacking in 2016: None identified, although last year's federal indictment of several Russian operatives stated that in October 2016 they "visited the websites of certain counties in Georgia, Iowa and Florida to identify vulnerabilities."
Security enhancements since: All the state's electronic voting machines are on track to get replaced before the March 24 presidential primary.
Voting paper trail: The new voting equipment prints out paper ballots, providing a way to audit election results.
Spending federal grants: Mostly for the new voting machines.
Quote: "I realize in an advanced-technology society that hackers never sleep and therefore nor can we. It is a constant battle to ensure the security of our voter database and election machines," said GOP Secretary of State Brad Raffensperger.
Iowa
Hacking in 2016: None identified, although an indictment spawned by special counsel Robert Mueller's investigation said Russian operatives went looking for election system vulnerability in the state.
Security enhancements since: The voter registration database has been replaced and security warning sensors have been attached to state election computers.
Voting paper trail: Paper ballots are the rule in all 99 counties.
Spending federal grants: To help pay for the new registration database, establish a two-factor access system for that system and to provide cybersecurity training for election officials.
Quote: "The Russians didn't hack a single vote, but they hacked our minds" last time, said GOP Secretary of State Paul Pate. "If they sow doubt about the integrity of our elections, they will disenfranchise voters."Michigan
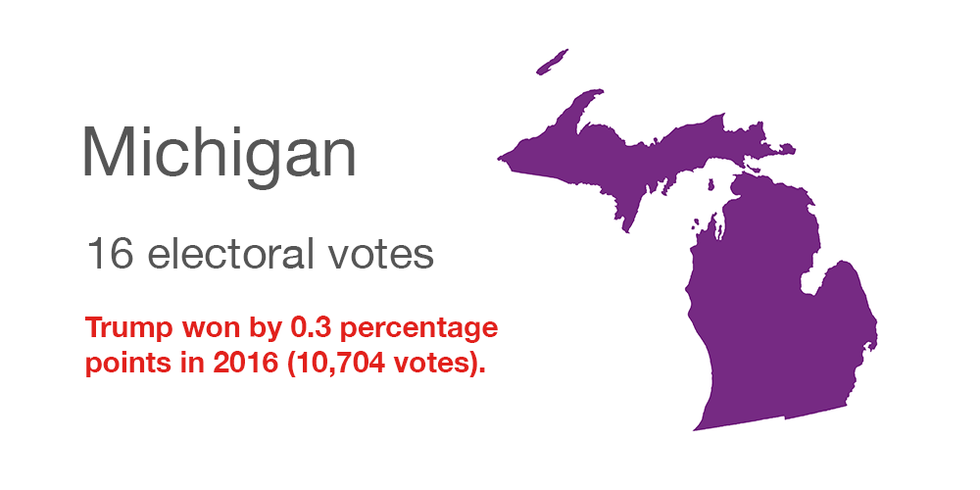
Hacking in 2016: None confirmed, but researchers found some patterns in the presidential voting that suggested possible interference.
Security enhancements since: The voter registration database has been modernized and touch-screen machines have been replaced with hand-marked ballots that are scanned.
Voting paper trail: Paper ballots are used statewide.
Spending federal grants: To improve the state's voter registration database and to provide funding and resources statewide for the completion of detailed election system security assessments at the state, county and local level.
Quote: "The threats to our elections did not end in 2016, and they will continue to evolve, and we must be prepared," said Democratic Secretary of State Jocelyn Benson.
Minnesota

Hacking in 2016: None uncovered, although this was one of the 21 states the Department of Homeland Security later identified as being targeted by Russians.
Security enhancements since: A cyberdefense team, including the secretary of state and the Minnesota National Guard, has been created to look for and address vulnerabilities.
Voting paper trail: Paper is the only type of ballot that gets used.
Spending federal grants: To hire a cybersecurity expert to help local officials, install software to warn of potential attacks, require an extra level of security for access to election computer systems and upgrade the state voter registration database.
Quote: "The plan is good, and the fundamentals of our system are good as well," Democratic Secretary of State Steve Simon said of the 2020 preparations. "We think we will have a secure election, but there is never any guarantee of any outcome."
Nevada

Hacking in 2016: None has come to light.
Security enhancements sinc e: All county election offices joined cybersecurity program offered by the nonprofit Center for Internet Security.
Voting paper trail: Voter-verifiable paper records are generated by the machines in all 16 counties.
Spending federal grants: To purchase new voting equipment, improve election auditing procedures and bolster security for the voter registration database.
Quote: "When it comes to security, oftentimes people are your weakest link," said Wayne Thorley, deputy secretary of state for elections. "It's important to have that ongoing training."New Hampshire
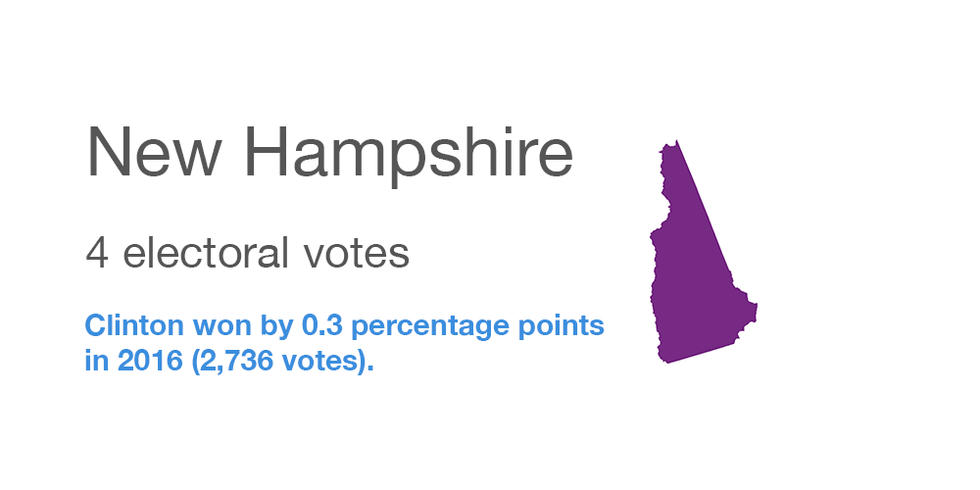
Hacking in 2016: None has come to light.
Security enhancements since: Security training has been conducted for the town and city clerks who administer elections.
Voting paper trail: Paper ballots are used statewide.
Spending federal grants: To hire a firm to assess the vulnerability of the state to election hacking and to install software that can provide a warning of an attempted attack.
Quote: "We strongly believe that elections are the purview of the states and that states should run their own elections," Deputy Secretary of State Dave Scanlan said. "The concerns we've had in the past with the federal government is not necessarily their involvement but the way the involvement seems to have occurred. We just want to make sure that what they're offering and what we might accept doesn't somehow lead to a federalization of the election process."
North Carolina
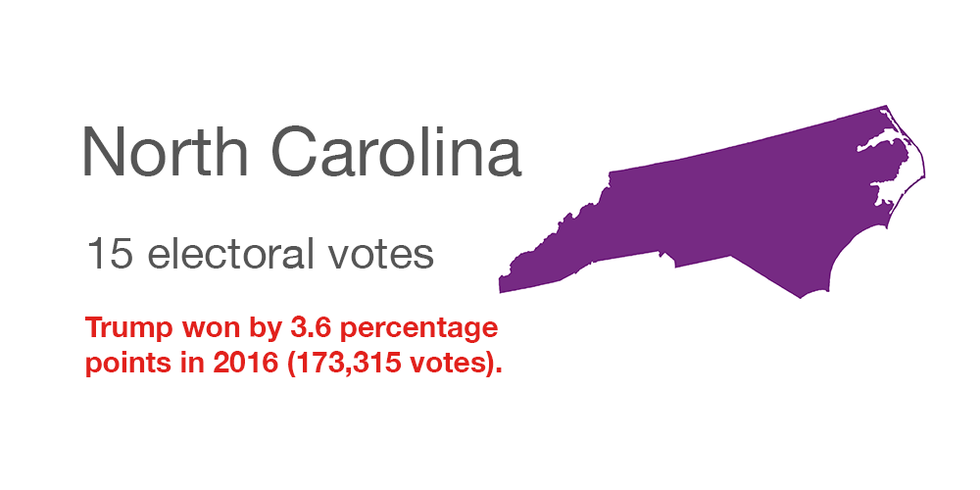
Hacking in 2016: None has been revealed, although investigations continue. This summer the Department of Homeland Security agreed to conduct an inspection of election equipment supplied by one of the state's vendors, Florida-based VR Systems, whose system was targeted by Russian hackers in 2016. VR Systems laptops used for checking in voters at polling places listed some as having already voted.
Security enhancements since: Additional post-election auditing measures are being prepared for use next year and the state's main election information system will be upgraded. Also, a chief information security position is being created.
Voting paper trail: Machines that generate a voter-verifiable paper record are deployed at polling places statewide.
Spending federal grants: To modernize state election management system and to improve post-election audits.
Quote: "We want all the voters to know all the steps we're taking to ensure fair and accurate elections, so voters will be confident that their vote counts," Board of Elections Executive Director Karen Brinson Bell said of her office's efforts to publicize the coming election system security improvements.
Ohio
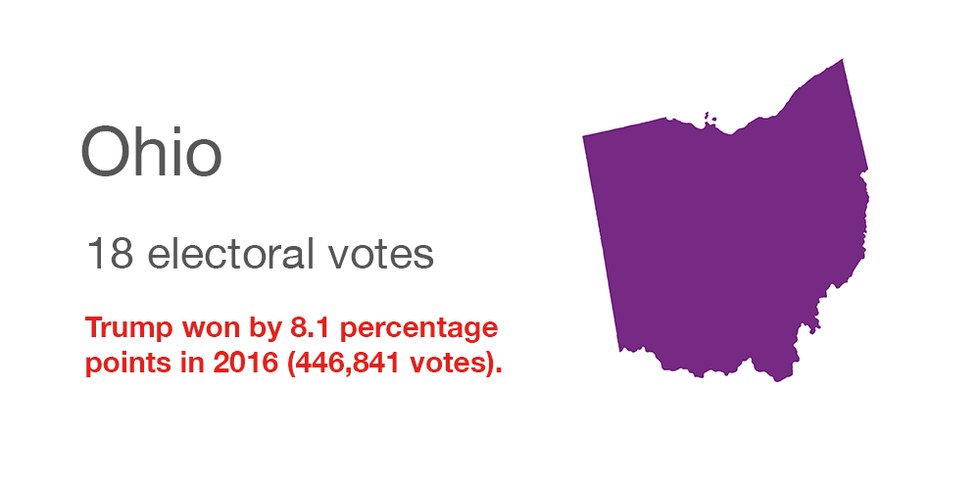
Hacking in 2016: None identified, but the state made the Homeland Security Department's roster of 21 known to have been checked for vulnerabilities by the Russians.
Security enhancements since: That state has made a number of upgrades: new voting machines; grants to counties to complete election security projects; legislation signed in October to promote more resilience in case of cyberattacks on election systems and to establish a chief information security officer in the secretary of state's office.
Voting paper trail: Machines that generate a voter-verifiable paper record are now in use across the state.
Spending federal grants: To conduct election security assessments for each county, buy devices to detect computer hacking attempts, expand cybersecurity training and improve the security of the voter registration database.
Quote: "Imagine looking out the window and seeing foreign paratroopers parachuting into your town," said Republican Secretary of State Frank LaRose. "We wouldn't tell a community, 'You're on your own — your sheriff's department can fight off that threat.' Well likewise, in the online world, we can now respond with Ohio's best cyber warriors, so these counties and cities have the support they need."
Pennsylvania
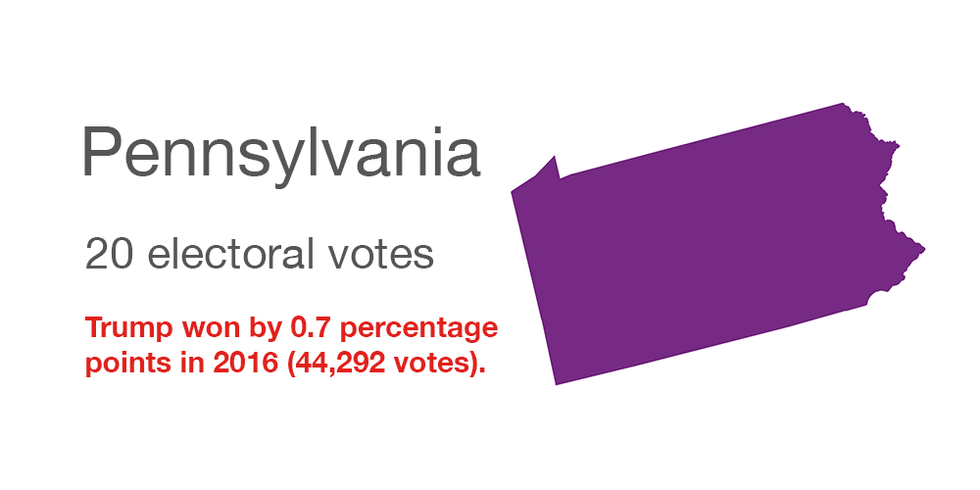
Hacking in 2016: None identified, but the state is on the Homeland Security Department's list of 21 where Russia went in search of election system vulnerabilities.
Security enhancements since: Counties were ordered to boost voting system safeguards, including by having devices that can detect hacking attempts. And the state is replacing almost all its touch-screen voting equipment.
Voting paper trail: Electronic machines that generate a paper record of each ballot are being purchased, with a goal of getting them installed in all 67 counties by November.
Spending federal grants: To buy and deploy the new voting booths.
Quote: "The Department of State has worked diligently over the past two years to increase election security in Pennsylvania and keep pace with the latest advances in cybersecurity," said the Democrat in charge of the office, Kathy Boockvar.Wisconsin
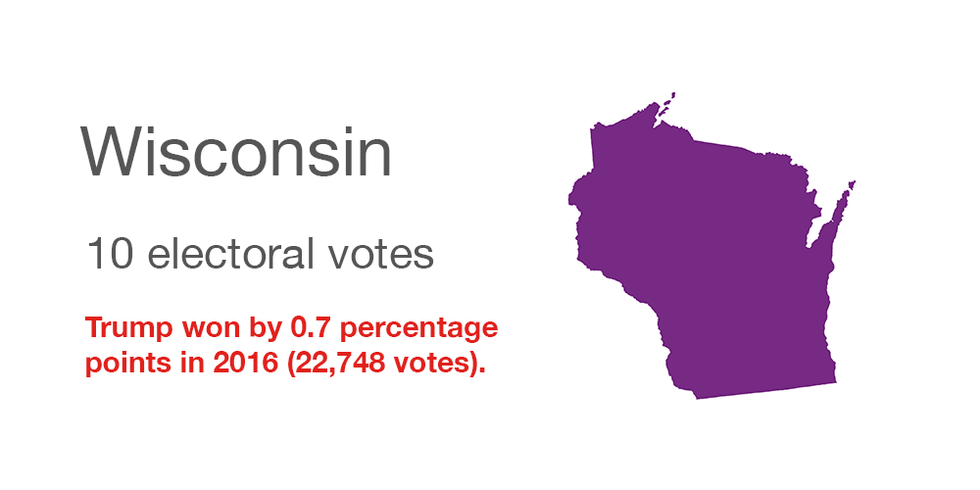
Hacking in 2016: There has been lots of innuendo but little proof. The Homeland Security Department says Wisconsin was among 21 states targeted by the Russian government but not penetrated. And two further attempts were made but neither succeeded. NBC News reported in 2018 that the state was among seven whose systems were compromised but that report was disputed, and no hard evidence has been revealed.
Security enhancements since: Officials are working on numerous areas including planning additional election safeguards and readying responses to attacks. The state has also launched a security training program for county and municipal election officials.
Voting paper trail: All polling places have voting machines that generate a voter-verifiable paper record.
Spending federal grants: To hire several additional information technology staffers to work on election security, develop stronger security to prevent hacking and provide additional security training to election officials.
Quote: "Defending democracy here in the state of Wisconsin is all our responsibility and something we take really seriously," said Meagan Wolfe, administrator of the Wisconsin Elections Commission. "None of us are going to stand for anybody compromising our democracy."















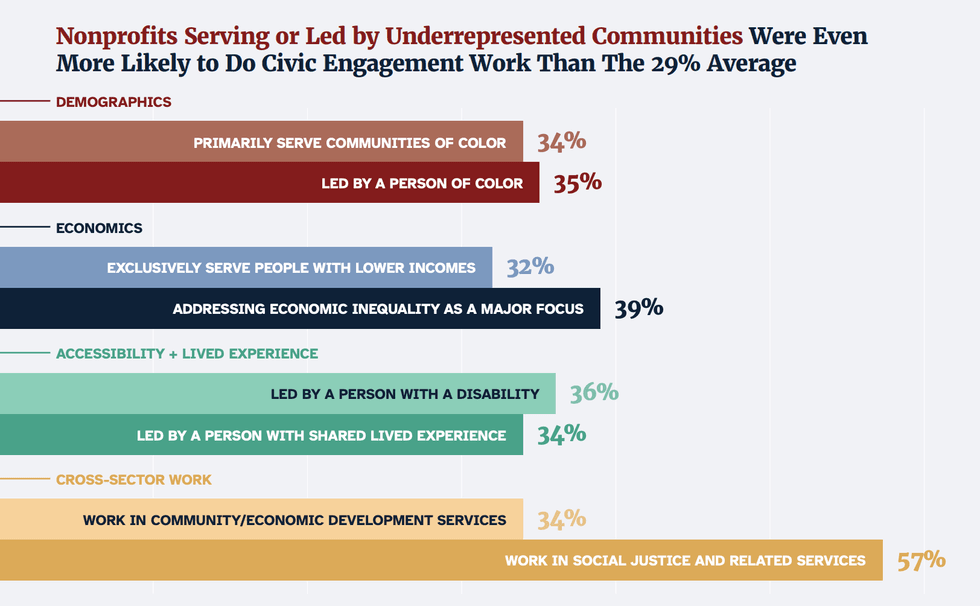 "On the Frontlines of Democracy" by Nonprofit Vote,
"On the Frontlines of Democracy" by Nonprofit Vote,

Trump & Hegseth gave Mark Kelly a huge 2028 gift